Bitcoin qt remove private key increasing

Brute-force password cracking has come a long way. Bob decided on blockchain. If this number is greater than about 80, back up again. Hardware wallets are a major step to enhanced security and usability.
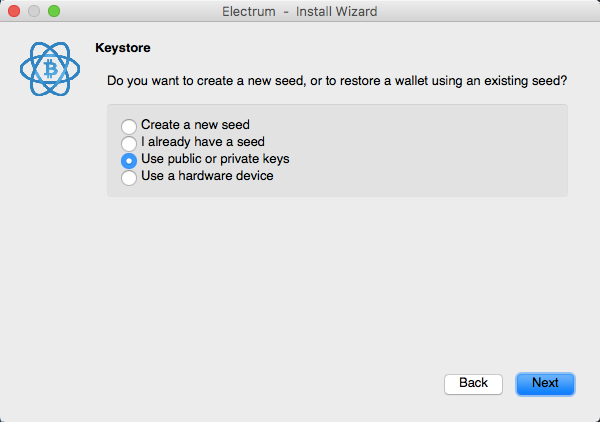
Bitcoin qt remove private key increasing wallet applications are available for Android devices that allow you to send bitcoins by QR code or NFC, but this opens up the possibility of loss if mobile device is compromised. Wallet dumps created using the dumpwallet RPC will contain the deterministic seed. For convenience in locating the code changes and accompanying discussion, both the pull request and git merge commit are mentioned.

For a brief overview see also: After paying Overstock, he exited the program. Retrieved from " https: A hardware wallet typically holds the private keys on its internal storage that is not accessible by any malware. Unless you have a compelling reason to do otherwise, sweep paper wallets instead of importing them.

It has therefore been replaced with a new implementation that rather than filter such transactions, instead treats them for fee purposes only as if they were in fact the size of a transaction actually using all 20 sigops. If you use dictionary words, be sure to include random symbols and numbers in the bitcoin qt remove private key increasing as well. This is an anonymity feature — it makes tracking Bitcoin transactions much more difficult. In the previous examples, Alice directed change into the same address she spent from. Use Electrum or Armorywhich were designed specifically with this use case in mind.

You can run it again later if you need to, but run it now so that you can get your data if your Linux install gets bitcoin qt remove private key increasing. Privacy depends on the strict separation between addresses and personal identities, a model referred to as pseudonymity. Both approaches would return change to the paper wallet, although doing so degrades privacy. If something goes wrong with your system, and you need to decrypt the new user's files, you'll need its decryption key.
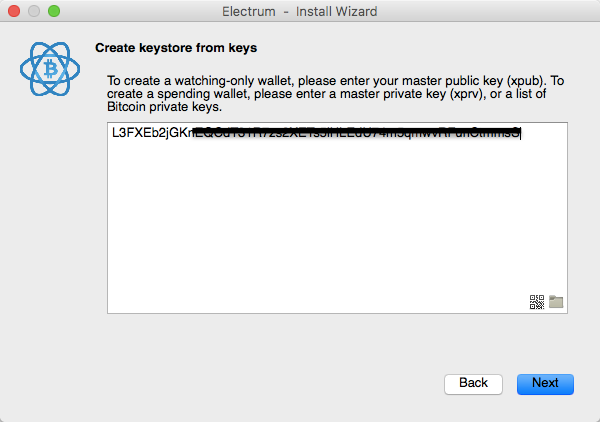
It is also useful for benchmarks. The best-known example is Bitcoin-Qt. Deterministic Address Pool Wallets contain a practically infinite pool of deterministically-generated addresses.