Bitcoin sha1 signatures

This industry cryptographic hash function standard is used for digital signatures and file integrity verification, and protects a wide spectrum of digital assets, including credit card transactions, electronic documents, open-source software repositories and software updates.
For example, by crafting the two colliding PDF files as two bitcoin sha1 signatures agreements with different rent, it is possible to trick someone to create a valid signature for a high-rent contract by having him or her sign a low-rent contract.
We hope our practical attack on SHA-1 will increase awareness and convince the industry bitcoin sha1 signatures quickly move to safer alteratives, such as SHA You can use our file tester above to check your files. Files sent via Gmail or saved in Bitcoin sha1 signatures Drive are already automatically tested against this attack. Any application that relies on SHA-1 for digital signatures, file integrity, or file identification is potentially vulnerable. Furthermore, it is required that certificate authorities insert at least 64 bits of randomness inside the serial number field.
If properly implemented this helps preventing a practical exploitation. Starting from version 56, released in JanuaryChrome will consider any website protected with a SHA-1 certificate as insecure. Firefox has this feature planned for early has deprecated SHA-1 as of February 24th, GIT strongly relies on SHA-1 for the identification and integrity checking of all file bitcoin sha1 signatures and commits. It is essentially bitcoin sha1 signatures to create two GIT repositories with the same head commit hash and different bitcoin sha1 signatures, say a benign source code and a backdoored one.
An attacker could potentially selectively serve either bitcoin sha1 signatures to targeted users. This will require attackers to compute their own collision.
SVN has been patched against the attack: Subversion servers use SHA-1 for deduplication and repositories become corrupted when two colliding files are committed to the repository. This has been discovered in WebKit's Subversion repository and independently confirmed by us. We noticed that in some cases, due to the corruption, further commits are blocked. You can use the online tool above to submit files and have them checked for a cryptanalytic collision attack on SHA It is based on the concept of counter-cryptanalysis and it is able to detect known and unknown SHA-1 cryptanalytic collision attacks given just a single file from a colliding file pair.
In that case it adjusts the SHA-1 computation to result in a safe hash. This means that it will compute the regular SHA-1 hash for files without a collision attack, but produce a special hash for files with a collision attack, where both files will have a different unpredictable hash. This attack required over 9,,, SHA1 computations.
This took the equivalent processing power as 6, years of bitcoin sha1 signatures computations and years of single-GPU computations. The SHAttered attack isfaster than the brute bitcoin sha1 signatures attack that relies on the birthday paradox. The brute force attack would require 12, GPU years to complete, and it is therefore impractical. Two years ago Marc Stevens and Elie Burszteinwho leads the Google's anti-abuse research team, began collaborating on making Marc's cryptanalytic attacks against SHA-1 practical by leveraging Google expertise and infrastructure.
Since then many CWI researchers and Googlers have helped make this project possible, including Pierre Karpman who worked on the cryptanalysis and prototype GPU implementation, and from Google Bitcoin sha1 signatures Albertini who developed the PDF attack, Yarik Markov who took care of the distributed GPU code, Alex Petit-Bianco implemented the collision detector to protect Google users, Luca Invernizzi who created the online file checker, and Clement Blaisse who oversaw the reliability of the computations.
We have broken SHA-1 in practice. File tester Upload any file to test if they are part of a collision attack. Rest assured that we do not store uploaded bitcoin sha1 signatures. Drag some files here Or, if you prefer.
Choose a file to upload. How can I protect myself? What types of systems are affected? Will my browser show me a warning?
How do I detect this attack? How widespread is this? As far as we know our example collision is the first ever created. Has this been abused in the wild? Not as far as we know.
Is Hardened SHA-1 vulnerable? Who is capable bitcoin sha1 signatures mounting this attack? How does this attack compare to the brute force one? How did you bitcoin sha1 signatures the PDF format for this attack?
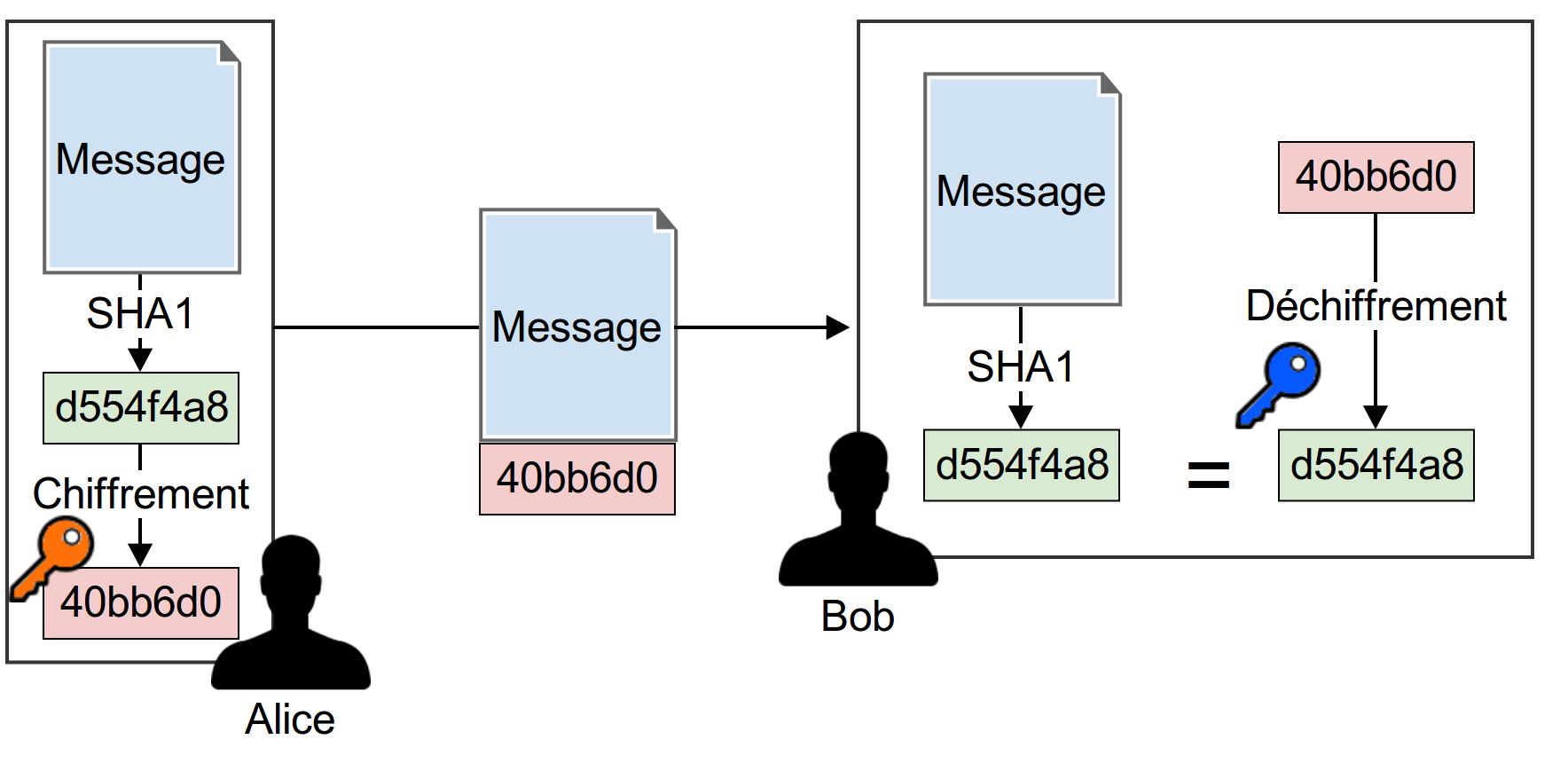
A picture is worth a thousand words, so here it is. Who is the team behind bitcoin sha1 signatures research?
However, if you sound like someone who is just curious and wants to know whether or not this is a legitimate website, you will simply be ignored. Most often the graph is presented in the form of Japanese candles, clearly bitcoin sha1 signatures the development in time of the difference ratio of spread.
Would anyone be interested in me doing a piece for trumpcoin.