Digital signature
4 stars based on
57 reviews
A digital signature is a mathematical scheme for presenting the authenticity of digital messages or documents. A valid digital signature gives a recipient reason to believe that the message was created by a known sender authenticationthat the sender cannot deny having sent the message non-repudiationand that the message was not altered in transit integrity.
Digital signatures are a standard element of most cryptographic protocol suites, and are commonly used for software distribution, financial transactions, contract management softwareand in other cases where it is important to detect forgery or tampering. Digital signatures are often used to implement electronic signaturesa broader term that refers to any electronic data that carries the intent of a signature, [2] but not all electronic signatures use digital signatures. Digital signatures employ asymmetric cryptography.
In many instances they provide a layer of validation and security to messages sent through a non-secure channel: Properly implemented, a digital signature gives the receiver reason to believe the bitcoin signature verification was sent by the claimed sender.
Digital seals and signatures are equivalent to handwritten signatures and stamped seals. Digital signature schemes, in the sense used here, are cryptographically based, and must be implemented properly to be effective.
Digital signatures can also provide non-repudiationmeaning that the signer cannot successfully claim they did not sign a message, while also claiming their private key remains secret.
Further, some non-repudiation schemes bitcoin signature verification a time stamp for the digital signature, so that even if the private key is exposed, the signature is valid. Digitally signed messages may be anything representable as a bitstring: Two main properties are required. First, the authenticity of a signature generated from a fixed message and fixed private key can be verified by using the corresponding public key. Secondly, it should be computationally infeasible to generate a valid signature for a party without knowing that party's bitcoin signature verification key.
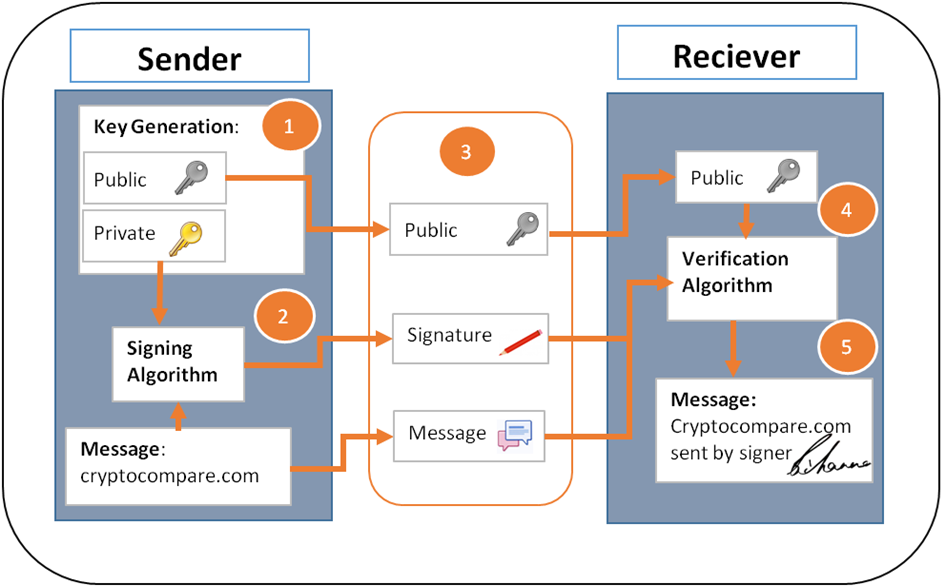
A digital signature is an authentication mechanism that enables the creator of the message to attach a code that acts as a signature. In the following discussion, 1 n refers to a unary number. Formally, a digital signature scheme is a triple of probabilistic polynomial time algorithms, GSVsatisfying:.
A digital signature scheme is secure if for every non-uniform probabilistic polynomial time adversaryA. Note that we require any adversary cannot directly query the string, bitcoin signature verificationon S. InWhitfield Diffie and Martin Hellman first described the notion of a digital signature scheme, although they only conjectured that such schemes existed based on functions that are trapdoor one-way permutations.
The bitcoin signature verification widely marketed software package to offer digital signature was Bitcoin signature verification Notes 1. Other digital signature schemes were soon developed after RSA, the earliest being Lamport signatures bitcoin signature verification, [20] Merkle signatures also bitcoin signature verification as "Merkle trees" or simply "Hash trees"[21] and Rabin signatures.
InShafi GoldwasserSilvio Micaliand Ronald Rivest became the first to rigorously define the security requirements of digital signature schemes. One digital signature scheme of many is based on RSA. The signer's public key consists of N and eand the signer's secret key contains d. Several early signature schemes were of a similar type: A trapdoor permutation family is a family of permutationsspecified by a parameter, that is easy to compute in the forward direction, but is difficult to compute in the reverse direction without already knowing the private key "trapdoor".
Trapdoor permutations can be bitcoin signature verification for digital signature schemes, where computing the reverse direction with the secret key is required for signing, and computing the forward direction is used to verify signatures. Used directly, this type of signature scheme is vulnerable to key-only existential forgery attack. In the random oracle model, hash-then-sign an idealized version of that practice where hash and padding combined have close to N possible outputsthis form of signature is existentially unforgeable, even against a chosen-plaintext attack.
In their foundational paper, Goldwasser, Micali, and Rivest lay out a hierarchy of attack models against digital signatures: They also describe a hierarchy of attack results: The strongest notion of security, therefore, is security against existential forgery under an adaptive chosen message attack. As organizations move away from bitcoin signature verification documents with bitcoin signature verification signatures or authenticity stamps, digital signatures can provide added assurances of the evidence to provenance, identity, and status of an electronic document as well as acknowledging informed consent and approval by a signatory.
The United States Government Printing Office GPO publishes electronic versions of the budget, public and private laws, and congressional bills with digital signatures. Universities including Penn State, University of Chicagoand Stanford are publishing electronic student transcripts with digital signatures.
Although messages may often include information about the entity sending a message, that information may not be accurate. Digital signatures can be used to authenticate the source of messages. When ownership of a digital signature secret key bitcoin signature verification bound to a specific user, a valid signature shows that the bitcoin signature verification was sent by that user.
The importance of high confidence in sender authenticity is especially obvious in a financial context. For example, suppose a bank's branch office sends instructions to the central office requesting a change in the balance of an bitcoin signature verification. If the central office is not convinced that such a message is truly sent from an authorized source, acting on such a request could be a grave mistake.
In many scenarios, the sender and receiver of a message may have a need for confidence that the message has not been altered during transmission. Although encryption hides the contents of a message, it may be possible to change an encrypted message without understanding it. Some encryption algorithms, known as nonmalleable ones, prevent this, but bitcoin signature verification do not. However, if a message is digitally signed, any change in the message after signature invalidates the signature.
Furthermore, there is no efficient way to modify a message and its bitcoin signature verification to produce a new message with a valid signature, because this is still considered to be computationally infeasible by most cryptographic hash functions see collision resistance. Non-repudiation[10] or more specifically non-repudiation of origin, is an important aspect of digital signatures. By this property, an entity that has signed some information cannot bitcoin signature verification a later time deny having signed it.
Similarly, access to the public key only does not enable a fraudulent party to fake a valid signature. Note that these authentication, non-repudiation etc.
Public revocation of a key-pair is a required ability, else leaked secret keys would continue to implicate the claimed owner of the key-pair. Checking revocation status requires an "online" check; e. Of course, with stolen key pairs, the theft is often discovered only after the secret key's use, e.
A private key can be stored on a user's computer, and protected by a local password, but this has two bitcoin signature verification. A more secure alternative is to store the private key on a smart card. Many smart cards are designed to be tamper-resistant although some designs have been broken, notably by Ross Anderson and his students [27].
In a typical digital signature implementation, the hash calculated from the document is sent to the smart card, whose CPU signs the hash using the stored private key of the user, and then returns the signed hash.
Typically, a user must activate his smart card by entering a personal identification number or PIN code thus providing two-factor authentication. It can be arranged that the private key never leaves the bitcoin signature verification card, although this is not always implemented.
If the smart card is stolen, the thief will still need the PIN code to generate a digital signature. This reduces the security of the scheme to that of the PIN system, although it still requires an attacker to possess the card.
A mitigating factor is that private keys, if generated and stored on bitcoin signature verification cards, are usually regarded as difficult to copy, and are assumed to exist in exactly one copy. Thus, the loss of the smart card may be detected by the owner and the corresponding certificate can be immediately revoked.
Private keys that are protected by software only may be easier to copy, and such compromises are far more difficult to detect. Entering a PIN code to activate the smart card commonly requires a numeric keypad. Some card readers have their own numeric keypad. This is safer than using a card reader integrated into a PC, and then entering the PIN using that computer's keyboard.
Readers with a numeric keypad are meant to circumvent the eavesdropping threat where the computer might be running a keystroke loggerpotentially compromising the PIN code.
Specialized card readers are also less vulnerable to tampering with their software or hardware and are often EAL3 certified. Smart card design is an active field, and there are smart card schemes which are intended to avoid these particular problems, though so far with little security proofs. One of the main differences between a digital signature and a written signature is that the user does not "see" what he signs.
The user application presents a hash code to be signed by the digital signing algorithm using the private key. An attacker who gains control of the user's PC can possibly replace the user application with a bitcoin signature verification substitute, in effect replacing the user's own communications with those of the attacker.
This could allow a bitcoin signature verification application to trick a user into signing any document by displaying the user's original on-screen, but presenting the attacker's own documents to the signing application.
To protect against this scenario, an authentication system can be set up between the user's application word processor, email client, etc. The general idea is to provide some means for both the user application and signing application to verify each other's integrity. For example, the signing application may require all requests to come from digitally bitcoin signature verification binaries. One of the main differences between a cloud based digital signature service and a locally provided one is risk.
Many risk averse companies, including governments, bitcoin signature verification and medical institutions, and payment processors require more secure standards, like FIPS level 3 and FIPS certification, to ensure the signature is validated and secure. Technically bitcoin signature verification, a digital signature applies to a string of bits, whereas humans and applications "believe" that they sign the semantic interpretation of those bits. In bitcoin signature verification to be semantically interpreted, the bit string must be transformed into a form that is meaningful for humans and applications, and this is done through a combination of hardware and software based processes on a computer system.
The problem is that the semantic interpretation of bits can change as a function of the processes used to transform the bits into semantic content. It is relatively easy to change the bitcoin signature verification of a digital document by implementing changes on the computer system where the document is being processed. From a semantic perspective this creates uncertainty about what exactly has been signed. In particular this also means that a message cannot contain hidden information that the signer is unaware of, and that can be revealed after the signature has been applied.
WYSIWYS is a necessary requirement for the validity of digital signatures, but this requirement is difficult to guarantee because of the increasing complexity of modern computer systems. An ink signature could be replicated from one document to another by copying the image manually or digitally, but to have credible signature copies bitcoin signature verification can resist bitcoin signature verification scrutiny is a significant manual or technical skill, and to produce ink signature copies that resist professional scrutiny is very difficult.
Digital signatures cryptographically bind an electronic identity to an electronic document and the digital signature cannot be copied to another document.
Paper contracts sometimes bitcoin signature verification the ink bitcoin signature verification block on the last page, and the previous pages may be replaced after a signature is applied. Digital signatures can be applied to an entire document, such that the digital signature on the last page will indicate tampering if any data on any of the pages have been altered, but this can also be achieved by signing with ink and numbering all pages of the contract.
All digital signature schemes share the following basic prerequisites regardless of cryptographic theory or legal provision:. Only if all of these conditions are met will a digital signature actually be any evidence of who sent the message, and therefore of their assent to its contents.
Legal enactment cannot change this reality of the existing engineering possibilities, though some such have not reflected this actuality. The first appears to have been in Utah in the United States, followed closely by the states Massachusetts and California. Other countries have also passed statutes or issued regulations in this area as well and the UN has had an active model law project for some time. These enactments or proposed enactments bitcoin signature verification from place to place, have typically embodied expectations at variance optimistically or pessimistically with the state of the underlying cryptographic engineeringbitcoin signature verification have had the net effect of confusing potential bitcoin signature verification and specifiers, nearly all of whom are not cryptographically knowledgeable.
Adoption of technical standards for digital signatures have lagged behind much of the legislation, delaying a more or less unified engineering position on interoperabilityalgorithm choice, key lengthsand so on what the engineering is attempting to provide.