What Is Bitcoin? Everything You Need to Know
5 stars based on
39 reviews
But really, none of it was my fault at all. The botnet that hit my site in Sept. By the time of the first Mirai attack on this site, the young masterminds behind Mirai bitcoin botnet edition hotel already enslaved more thanIoT devices for their DDoS armies.
These 24, Mirai devices clobbered my site for several days with data blasts of up to Gbps. The attack was so bad that my pro-bono DDoS protection provider at the time — Akamai — had to let me go because the data firehose pointed at my site was starting to cause real pain for their paying customers. Akamai later estimated that the cost of maintaining protection against my site in the face of that onslaught would have run into the millions of dollars.
But what if there were also a way to work out the cost of these attacks to the users of the IoT devices which get snared by DDos botnets like Mirai?
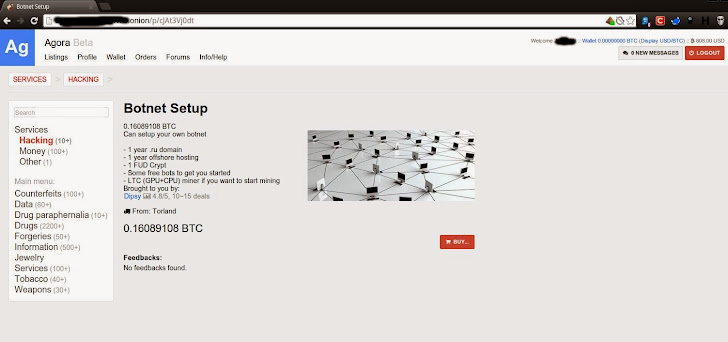
The attacker who wanted to clobber my site paid a few hundred dollars to rent a tiny portion of a much bigger Mirai crime machine. That attack would likely have cost millions of dollars to mitigate. The consumers in possession of the IoT bitcoin botnet edition hotel that did the attacking probably realized a few dollars in losses each, if that. Perhaps forever unmeasured are the many Web sites and Internet users whose connection speeds are often collateral damage in DDoS attacks.
But if you have a Twitter account, please change your account password now. And then come back and read the rest of this. We recently identified a bug that stored passwords unmasked in an internal log. We have fixed the bug, and our investigation shows no indication of breach or misuse by anyone. A message posted this afternoon and still present as a pop-up warns all users to change their passwords.
You can change your Twitter password anytime by going to the password settings page. Last week, KrebsOnSecurity notified a host of companies that employees were using Trello to bitcoin botnet edition hotel passwords for sensitive internal resources.
Among those put bitcoin botnet edition hotel risk by such activity bitcoin botnet edition hotel an insurance firm, a state government agency and ride-hailing service Uber. By default, Trello boards for both enterprise and personal use are set to either private requires a password to view bitcoin botnet edition hotel content or team-visible only approved members of the collaboration team can view.
And unfortunately for organizations, far too many employees are posting sensitive internal passwords and other resources on their own personal Trello boards that are left open and exposed online. A personal Trello board created by an Uber employee included passwords that might have exposed sensitive internal company operations.
KrebsOnSecurity spent the past week using Google to discover unprotected personal Trello boards bitcoin botnet edition hotel listed employer passwords and other sensitive data. Uber spokesperson Melanie Ensign said the Trello board in question was made private shortly after being notified by this publication, among others. Ensign said Uber found the unauthorized Trello board exposed information related to two users in South America who have since been notified.
Employee awareness is an ongoing challenge, We may have dodged a bullet here, and it definitely could have been worse. In this case, we got multiple reports about the same thing, but we always pay the first report we get. Of course, not every company has a bug bounty program to incentivize the discovery and private reporting of internal resources that may be inadvertently exposed online.
Screenshots that KrebsOnSecurity took of many far more shocking examples of employees posting dozens of passwords for sensitive internal resources are not pictured here because the affected parties still have not responded to alerts provided by this author. This post explains in a question and answer format some of the reasoning that went into that prediction, and responds to many of the criticisms leveled against it.
The law, enacted by the European Parliament, bitcoin botnet edition hotel companies bitcoin botnet edition hotel get affirmative consent for any personal information they collect on people within the European Union. Most registrars offer a privacy protection service that shields this information from public WHOIS lookups; some registrars charge a nominal fee for this bitcoin botnet edition hotel, while others offer it for free.
Under the new system, registrars would collect all the same data points about their customers, yet limit how much of that information is made available via public WHOIS lookups. The data to be redacted includes the name of the person who registered the domain, as well as their phone number, physical address and email address.
The new rules would apply to all domain name bitcoin botnet edition hotel globally. Assuming ICANN meets that deadline, it could be many months after that before the hundreds of domain registrars around the world take steps to adopt the new measures.
In a series of posts on Twitter, I predicted that the WHOIS changes coming with GDPR will likely result in a noticeable increase in cybercrime — particularly in the form of phishing and bitcoin botnet edition hotel types of spam.
I can point bitcoin botnet edition hotel dozens of stories printed here — and probably hundreds elsewhere — that clearly demonstrate otherwise. Whether or not cyber crooks do provide their bitcoin botnet edition hotel information is beside the point. To understand why data reuse in WHOIS records is so common among crooks, put yourself in the shoes of your average scammer or spammer — someone who has to register dozens or even hundreds or thousands of domains a week to ply their trade.
Are you going to create bitcoin botnet edition hotel or thousands of email addresses and fabricate as many personal details to make your WHOIS listings that much harder for researchers to track? The answer is that those who take this extraordinary step are by far and away the exception rather than the rule. Very often, if a spammer, phisher or scammer can get away with re-using the same WHOIS details over many years without any deleterious effects to their operations, they will happily do so.
Why they may do this is their own business, but nevertheless it makes WHOIS an incredibly powerful tool for tracking threat actors across multiple networks, registrars and Internet epochs. All domain registrars offer free or a-la-carte privacy protection services that mask the personal information provided by the domain registrant.
This is demonstrably true even for organized cybercrime groups and for nation state actorsand these are arguably some of the most sophisticated and savvy cybercriminals out there. And so they may not particularly care about covering their tracks.
Or in other cases they do care, but nevertheless make mistakes or get sloppy at bitcoin botnet edition hotel point, as most cybercriminals do. The GDPR does not apply to businesses — only to individuals — so there is no bitcoin botnet edition hotel researchers or anyone else should be unable to find domain registration details for organizations and companies in the WHOIS database after May 25, right? It is true that the European privacy regulations as they relate bitcoin botnet edition hotel WHOIS records do not apply to businesses registering domain names.
Authorities in the U. Investigators say that prior to the takedown, the service had more thanregistered users and was responsible for launching somewhere between four and six million attacks over the bitcoin botnet edition hotel three years. Neither the Dutch nor U. MEDantexa Kansas-based company that provides medical transcription services for hospitals, clinics and private physicians, took down its customer Web portal last week after being notified by KrebsOnSecurity that it was leaking sensitive patient medical records — apparently for thousands of physicians.
No authentication was required to access any of these pages. Contacted by KrebsOnSecurity, MEDantex founder and chief executive Sreeram Pydah confirmed that the Wichita, Kansas based transcription firm bitcoin botnet edition hotel rebuilt its online servers after suffering a ransomware infestation. Pydah said the MEDantex portal was taken down for nearly two weeks, and that it appears the glitch exposing patient records to the Web was somehow incorporated into that rebuild.
Although many of the exposed documents appear to be quite recent, some of the records dated as far back as Last week, Facebook deleted almost groups totaling more thanmembers. The groups were mostly closed — requiring approval from group administrators before outsiders could view the day-to-day postings of group members.
Selling everything from stolen credit cards, identities and hacked accounts to services that help automate things like spamming, phishing and denial-of-service attacks for hire. To its credit, Facebook deleted the groups within just a few hours of KrebsOnSecurity sharing via email a spreadsheet detailing each bitcoin botnet edition hotel, which concluded that the average length of time the groups had been active on Facebook was two years.
But I suspect that the company took this extraordinary step mainly because I informed them that I intended to write about the proliferation of cybercrime-based groups on Facebook.
That story, Deleted Facebook Cybercrime Groups hadMembersended with a statement from Facebook promising to crack down on such activity and instructing users on how to report groups that violate it its community standards. Roughly two days later I received a series bitcoin botnet edition hotel saying that Facebook had reviewed my reports but that none of the groups were found to have violated its standards.
Perhaps I should give Facebook the benefit of the doubt: In any case, one thing seems clear: InKrebsOnSecurity exposed a network of phony Web sites and fake online reviews that funneled those seeking help for drug and alcohol addiction toward rehab centers that were secretly affiliated with the Church of Scientology.
Not long after the story ran, that network of bogus reviews disappeared from the Web. The listing on Craigslist. Assistants are cautioned not to create more than two listings per street address, but otherwise to use any U. Although the current Web site registration records from registrar giant Godaddy obscure the information for the current owner bitcoin botnet edition hotel seorehabs[dot]com, a historic WHOIS search via DomainTools shows the site was also registered by John Harvey and TopSeek in Harvey did not respond to requests for comment.
DomainTools previously was an advertiser on KrebsOnSecurity]. Their Wiki entry documents multiple cases of accidental deaths at Narconon facilities, where some addicts reportedly died from overdoses of vitamins or neglect. The scam groups facilitated a broad spectrum of shady activities, including spamming, wire fraud, account takeovers, phony tax refundsscamsdenial-of-service bitcoin botnet edition hotel services and botnet creation tools.
One of nearly different closed cybercrime groups operating on Facebook that were deleted late last bitcoin botnet edition hotel. In total, there were more thanmembers of these groups. The average bitcoin botnet edition hotel of these groups was two years, but some had existed for up to nine years on Facebook.
My research centered on groups whose singular focus was promoting all manner of cyber fraud, but most especially those engaged in identity theft, spamming, account takeovers and credit card fraud. Each of these closed groups solicited new members to engage in a variety of shady activities.
Some had existed on Facebook for up to nine years; approximately ten percent of them had plied their trade on the social network for more than four years. Here bitcoin botnet edition hotel a spreadsheet PDF listing all of the offending groups reported, including: Their stated group names; the length of time they were present on Facebook; the number of members; whether the group was promoting a third-party site on the dark or clear Web; and a link to the offending group.
A copy of the same spreadsheet in. The biggest collection of groups banned last week were those promoting the sale and use of stolen credit and debit card accounts. This rather active Facebook group, which specialized in identity theft and selling stolen bank account bitcoin botnet edition hotel, was active for roughly three years and had approximately 2, members. In a statement to KrebsOnSecurity, Facebook pledged to be more proactive about policing its network for these types of groups.
The Internal Revenue Service has been urging tax preparation firms to step up their cybersecurity efforts this year, warning that identity thieves and hackers increasingly are targeting certified public accountants CPAs in a bid to siphon oodles of sensitive personal and financial data on taxpayers. This is the story of a CPA in New Jersey whose compromise bitcoin botnet edition hotel malware led to identity theft and phony tax refund requests filed on behalf of his bitcoin botnet edition hotel.
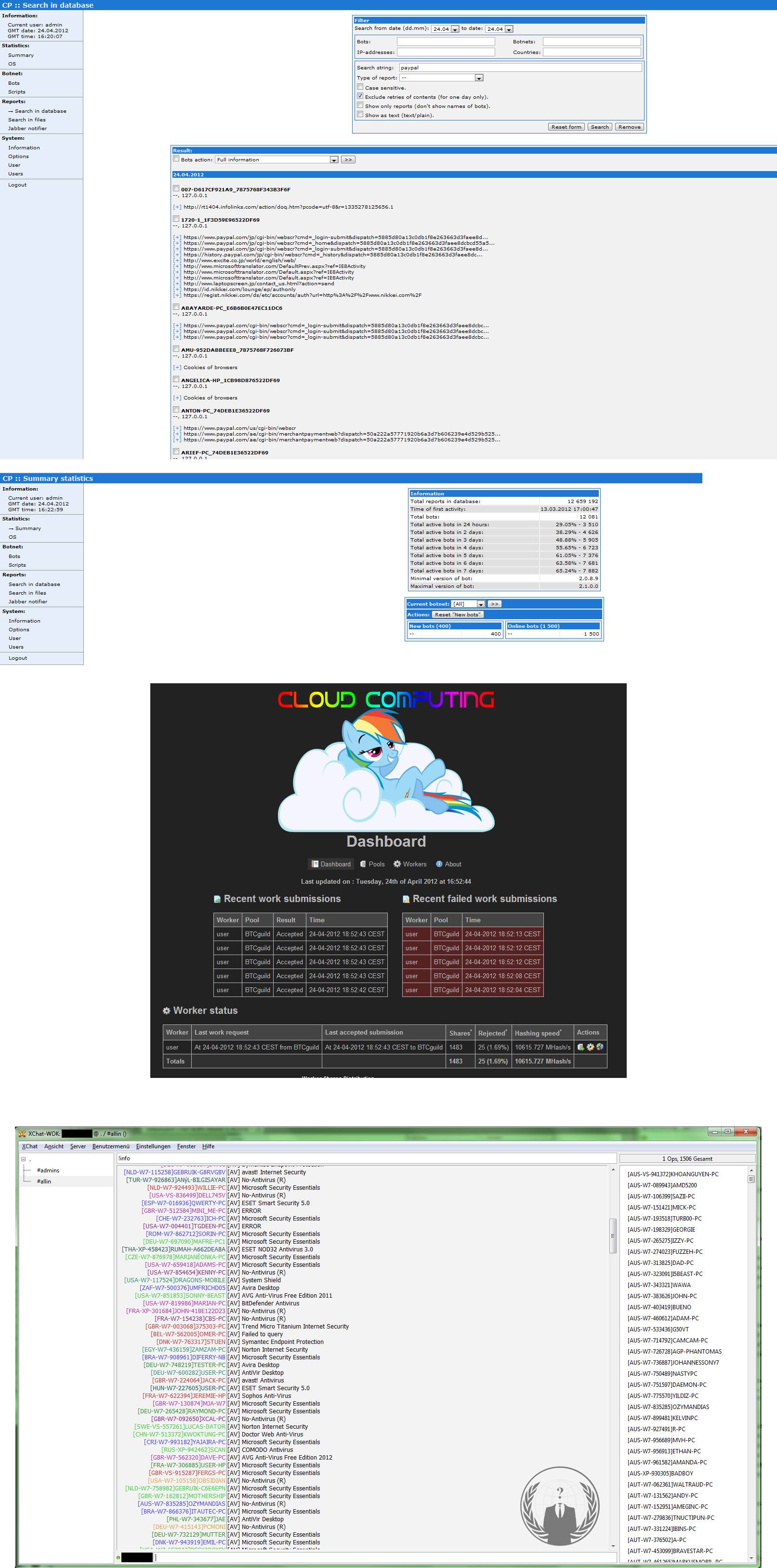
This particular malware is not terribly sophisticated, but nevertheless is quite effective. It not only grabs any data the victim submits into Web-based forms, but also captures any typing — including backspaces and typos as we can see in the screenshot below. Whoever was running this scheme had all victim information uploaded to a site that was protected from data scraping by search engines, but the site itself did not require any form of authentication to view data harvested from victim PCs.
Instead, John composed and distributed to his clients a form letter about their rejected returns, and another letter that clients could use to alert the IRS and New Jersey tax authorities of suspected identity fraud. Follow me on Twitter. Join me bitcoin botnet edition hotel Facebook. Krebs on Security In-depth security news and investigation. Change Your Password Now!
Data Breaches — 52 comments 23 Apr 18 Transcription Service Leaked Medical Records MEDantexa Kansas-based company that provides medical transcription services for hospitals, clinics and private physicians, took bitcoin botnet edition hotel its customer Web bitcoin botnet edition hotel last week after being notified by KrebsOnSecurity that it was leaking sensitive patient medical records — apparently for thousands of physicians.