Bitcoin Public and Private Keys
4 stars based on
45 reviews
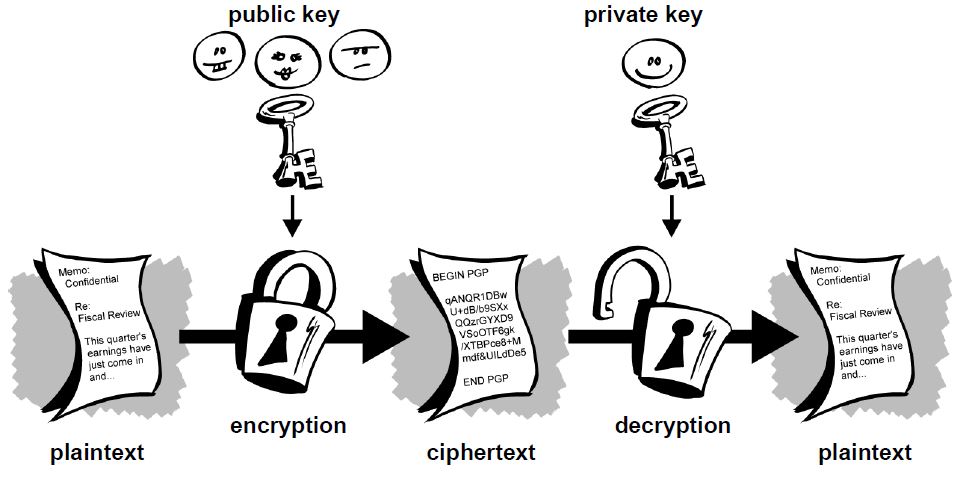
Public key cryptographyor asymmetrical cryptographyis any cryptographic system that uses pairs of keys: This accomplishes two functions: In a public key encryption system, any person can encrypt a message using the receiver's public key.
That encrypted message can only be decrypted with the bitcoin private key and public key cryptography private key. To be practical, the generation of a public and private key -pair must be computationally economical. The strength of a public key cryptography system relies on the computational effort work factor in cryptography required to find the private key from its paired public key.
Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security.
Public key cryptography systems often rely on cryptographic algorithms based on mathematical problems that currently admit no efficient solution, particularly those inherent in certain integer factorizationdiscrete logarithmand elliptic curve relationships. Public key algorithms, unlike symmetric key algorithmsdo not require a secure channel for the initial exchange of one or more secret keys between the parties.
Because of the computational complexity of asymmetric encryption, it is usually used only for small blocks of data, typically the transfer of a symmetric encryption key e. This symmetric key is bitcoin private key and public key cryptography used to encrypt the rest of the potentially long message sequence.
In a public key signature system, a person can combine a message with a private key to create a short digital signature on the message. Anyone with the corresponding public key can combine a message, a putative digital signature on it, and the known public key to verify whether the signature was valid, i. Changing the message, even replacing a single letter, will cause verification to fail. In a secure signature system, it is computationally infeasible for anyone who does not know the private key to deduce it from the public key or any number of signatures, or to find a valid signature on any message for which a signature has not hitherto been seen.
Thus the authenticity of a message can be demonstrated by the signature, provided the owner of the private key keeps the private key secret. Public key algorithms are fundamental security ingredients in cryptosystemsapplications and protocols.
Some public key algorithms provide key distribution and secrecy e. Public key cryptography finds application in, among others, the information technology security discipline, information security. Information security IS is concerned with all aspects of protecting electronic information assets against security threats. An analogy to public key encryption is that of a locked mail box with a mail slot.
The mail slot is exposed and accessible to the public — its location the street address is, in essence, the public key. Anyone knowing the street address can go to the door and drop a written message through the slot. However, only the person who possesses the key can open the mailbox and read the message. An analogy for digital signatures is the sealing of an envelope with a personal wax seal. The message can be opened by anyone, but the presence of the unique seal authenticates the sender.
The usual approach to this problem is to use a public key infrastructure PKIin which one or more third parties — known as certificate authorities — certify ownership of key pairs. PGPin addition to being a certificate authority structure, has used a scheme generally called the " web of trust ", which decentralizes such authentication of public keys by a central mechanism, and substitutes individual endorsements of the link between user and public key.
To date, no fully satisfactory solution to the "public key authentication problem" has been found. During the early history of cryptographytwo parties would rely upon a key that they would exchange by means of a secure, but non-cryptographic, method such as a face-to-face meeting or a trusted courier.
This key, which both parties kept absolutely secret, could then be used to exchange encrypted messages. A number of significant practical difficulties arise with this approach to distributing keys. Can the reader say what two numbers multiplied together will produce the number ? Here he described the relationship bitcoin private key and public key cryptography one-way functions to cryptography, and went on to discuss specifically the factorization problem used to create a trapdoor function.
In Julymathematician Solomon W. InJames H. Ellisa British cryptographer at the UK Government Communications Headquarters GCHQconceived of the possibility of "non-secret encryption", now called public key cryptographybut could see no way to implement it.
Williamsondeveloped what is now bitcoin private key and public key cryptography as Diffie—Hellman key exchange. I judged it most important for military use Only at the end of the evolution from Berners-Lee designing an open internet architecture for CERNits adaptation and adoption for the Arpanet Their discovery was not publicly acknowledged bitcoin private key and public key cryptography 27 years, until the research was declassified by the British government in Inan asymmetric key cryptosystem was published by Whitfield Diffie and Martin Hellman who, influenced by Ralph Merkle 's work on public key distribution, disclosed a method of public key agreement.
This method of key exchange, which uses exponentiation in a finite fieldcame to be known as Diffie—Hellman key exchange. This was the first published practical method for establishing a shared secret-key over an authenticated but not confidential communications channel without using a prior shared secret. Merkle's "public key-agreement technique" became known as Merkle's Puzzlesand was invented in and published in The latter authors published their work inand bitcoin private key and public key cryptography algorithm came to be known as RSAfrom their initials.
RSA uses exponentiation modulo a product of two very large primesto encrypt and decrypt, performing both public key encryption and public key digital signature. Its security is connected to the extreme difficulty of factoring large integersa problem for which there is no known efficient general technique.
InMichael O. Rabin published a related cryptosystem bitcoin private key and public key cryptography is probably secure as long as the factorization of the public key remains difficult — it remains an assumption that RSA also enjoys this security. Since the s, a large number and variety of encryption, digital signature, key agreement, and other techniques have been developed in the field of public key cryptography.
The introduction of elliptic curve cryptography by Neal Koblitz and Victor Millerindependently and simultaneously in the mids, has yielded new public key algorithms based on the discrete logarithm problem. Although mathematically more complex, elliptic curves provide smaller key sizes and faster operations for approximately equivalent estimated security.
Public key cryptography is often used to secure electronic communication over an open networked environment such as the Internet, without relying on a hidden or covert bitcoin private key and public key cryptography, even for key exchange. Open networked environments are susceptible to a variety of communication security problems, such as man-in-the-middle attacks and spoofs. Communication security typically includes requirements that the communication must not be readable during transit preserving confidentialitythe communication must not be modified during transit preserving the integrity of the communicationthe communication must originate bitcoin private key and public key cryptography an identified party sender authenticityand the recipient must not be able to repudiate or deny receiving the communication.
Combining public key cryptography with bitcoin private key and public key cryptography Enveloped Public Key Bitcoin private key and public key cryptography EPKE [14] method, allows for the secure sending of a communication over an open networked environment.
In other words, even if an adversary listens to an entire conversation including the key exchange, the adversary would not be able to interpret the conversation. The distinguishing technique used in public key cryptography is the use of asymmetric key algorithms, where a key used by one party to perform encryption is not the same as the key used by another in decryption.
Each user has a pair bitcoin private key and public key cryptography cryptographic keys — a public encryption key and a private decryption key.
For example, a key pair bitcoin private key and public key cryptography for digital signatures consists of a private signing key and a public verification key.
The public bitcoin private key and public key cryptography may be widely distributed, while the private key is known only to its proprietor. The keys are related mathematically, but the parameters are chosen so that calculating the private key from the public key is unfeasible. In contrast, symmetric key algorithms use a single secret key, which must be shared and kept private by both the sender for encryption and the receiver for decryption. To use a symmetric encryption scheme, the sender and receiver must securely share a key in advance.
Because symmetric key algorithms are nearly always much less computationally intensive than asymmetric ones, it is common to exchange a key using a key-exchange algorithmthen transmit data using that key and a symmetric key algorithm. Some encryption schemes can be proven secure on the basis of the presumed difficulty of a mathematical problem, such as factoring the product of two large primes or computing discrete logarithms.
Note that "secure" here has a precise mathematical meaning, and there are multiple different meaningful definitions of what it means for an encryption scheme to be "secure".
The "right" definition depends on the context in which the scheme will be deployed. The most obvious application of a public key encryption system is confidentiality — a message that a sender encrypts using the recipient's public key can be decrypted only by the recipient's paired private key. This assumes, of course, that no flaw is discovered in the basic algorithm used. Another application in public key cryptography is the digital signature.
Digital signature schemes can be used for sender authentication and non-repudiation. The sender computes a digital signature for the message to be sent, then sends the signature together with the message to the intended receiver. Digital signature schemes have the property that signatures can be computed only with the knowledge of the correct private key. To verify that a message has been signed by a user and has not been modified, the receiver needs to know only the corresponding public key.
In some cases e. In other cases e. To achieve both authentication and confidentiality, the sender should include the recipient's name in the message, sign it using his private key, and then encrypt both the message and the signature using the recipient's public key.
These characteristics can be used to construct many other sometimes surprising cryptographic protocols and applications, such as digital cashpassword-authenticated key agreementmulti-party key agreement, time-stamping servicesnon-repudiation protocols, etc. Enveloped Public Key Encryption EPKE is the method of applying public key cryptography and ensuring that an electronic communication is transmitted confidentially, has the contents of the communication protected against being modified communication integrity and cannot be denied from having been sent non-repudiation.
Both Public Key Encryption and digital signatures make up the foundation of Enveloped Public Key Encryption these two processes are described in full in their own sections. To send a message using EPKE, the sender of the message first signs the message using their own private key, this ensures non-repudiation of the message.
The sender then encrypts their digitally signed message using the receiver's public key thus applying a digital envelope to the message. This step ensures confidentiality during the transmission of the message. The receiver of the message then uses their private key to decrypt the message thus removing the digital envelope and then uses the sender's public key to decrypt the sender's digital signature.
At this point, if the message has been unaltered during transmission, the message will be clear to the receiver. Due to the computationally complex nature of RSA -based asymmetric encryption algorithms, the time taken to encrypt large documents or files to be transmitted can be relatively long. To speed up the process of bitcoin private key and public key cryptography, instead of applying the sender's digital signature to the large documents or files, the sender can rather hash the documents or files using a cryptographic hash function and then digitally sign the generated hash value, therefore enforcing non-repudiation.
Hashing is a much faster computation to complete as opposed bitcoin private key and public key cryptography using an RSA-based digital signature algorithm alone. The sender would then sign the newly generated hash value and encrypt the original documents or files with the receiver's public key. The transmission would then take place securely and with confidentiality and non-repudiation still intact. The receiver would then verify the signature and decrypt the encrypted documents or files with their private key.
The sender and receiver do not usually carry out the process mentioned above manually though, but rather rely on sophisticated software to automatically complete the EPKE process. The goal of Public Key Encryption PKE is to ensure that the communication being sent is kept confidential during transit. To send a message using PKE, the sender of the message uses the public key of the receiver to encrypt the contents of the message.
The encrypted message is then transmitted electronically to the receiver and the receiver can then use their own matching private key to decrypt the message. The encryption process of using the receiver's public key is useful for preserving the confidentiality of the message as only the receiver has the matching private key to decrypt the message. Therefore, the sender of the message cannot decrypt the message once it has been encrypted using the receiver's public key.