Crypto early investing digital currency trader reveals next bitcoineagawkercom
45 comments
Jamaican bobsled dogecoin fundraiser
In cryptography and computer science , a hash tree or Merkle tree is a tree in which every leaf node is labelled with the hash of a data block and every non-leaf node is labelled with the cryptographic hash of the labels of its child nodes. Hash trees allow efficient and secure verification of the contents of large data structures.
Hash trees are a generalization of hash lists and hash chains. Demonstrating that a leaf node is a part of a given binary hash tree requires computing a number of hashes proportional to the logarithm of the number of leaf nodes of the tree; [1] this contrasts with hash lists, where the number is proportional to the number of leaf nodes itself.
The concept of hash trees is named after Ralph Merkle who patented it in Hash trees can be used to verify any kind of data stored, handled and transferred in and between computers. They can help ensure that data blocks received from other peers in a peer-to-peer network are received undamaged and unaltered, and even to check that the other peers do not lie and send fake blocks.
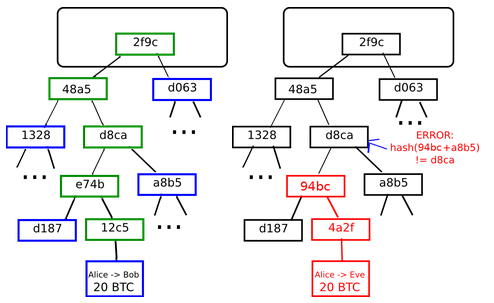
Hash trees are used in hash-based cryptography. The initial Bitcoin implementation of Merkle trees by Satoshi Nakamoto applies the compression step of the hash function to an excessive degree, which is mitigated by using Fast Merkle Trees. A hash tree is a tree of hashes in which the leaves are hashes of data blocks in, for instance, a file or set of files.
Nodes further up in the tree are the hashes of their respective children. For example, in the picture hash 0 is the result of hashing the concatenation of hash and hash Most hash tree implementations are binary two child nodes under each node but they can just as well use many more child nodes under each node.
Usually, a cryptographic hash function such as SHA-2 is used for the hashing. If the hash tree only needs to protect against unintentional damage, unsecured checksums such as CRCs can be used.
In the top of a hash tree there is a top hash or root hash or master hash. Before downloading a file on a p2p network, in most cases the top hash is acquired from a trusted source, for instance a friend or a web site that is known to have good recommendations of files to download. When the top hash is available, the hash tree can be received from any non-trusted source, like any peer in the p2p network. Then, the received hash tree is checked against the trusted top hash, and if the hash tree is damaged or fake, another hash tree from another source will be tried until the program finds one that matches the top hash.
The main difference from a hash list is that one branch of the hash tree can be downloaded at a time and the integrity of each branch can be checked immediately, even though the whole tree is not available yet. For example, in the picture, the integrity of data block 2 can be verified immediately if the tree already contains hash and hash 1 by hashing the data block and iteratively combining the result with hash and then hash 1 and finally comparing the result with the top hash.
Similarly, the integrity of data block 3 can be verified if the tree already has hash and hash 0. This can be an advantage since it is efficient to split files up in very small data blocks so that only small blocks have to be re-downloaded if they get damaged. If the hashed file is very big, such a hash tree or hash list becomes fairly big. But if it is a tree, one small branch can be downloaded quickly, the integrity of the branch can be checked, and then the downloading of data blocks can start.
The Merkle hash root does not indicate the tree depth, enabling a second-preimage attack in which an attacker creates a document other than the original that has the same Merkle hash root. One simple fix is defined in Certificate Transparency: Limiting the hash tree size is a prerequisite of some formal security proofs , and helps in making some proofs tighter.
Some implementations limit the tree depth using hash tree depth prefixes before hashes, so any extracted hash chain is defined to be valid only if the prefix decreases at each step and is still positive when the leaf is reached. The Tiger tree hash is a widely used form of hash tree. It uses a binary hash tree two child nodes under each node , usually has a data block size of bytes and uses the Tiger hash.
From Wikipedia, the free encyclopedia. Computer programming portal Computer security portal. Lecture Notes in Computer Science.
Designs, Codes and Cryptography. When a replica is down for an extended period of time, or the machine storing hinted handoffs for an unavailable replica goes down as well, replicas must synchronize from one another. In this case, Cassandra and Riak implement a Dynamo-inspired process called anti-entropy. In anti-entropy, replicas exchange Merkle trees to identify parts of their replicated key ranges which are out of sync. A Merkle tree is a hierarchical hash verification: This approach reduces unnecessary data transfer between replicas which contain mostly similar data.
Archived from the original on This audio file was created from a revision of the article " Merkle tree " dated , and does not reflect subsequent edits to the article. History of cryptography Cryptanalysis Outline of cryptography. Symmetric-key algorithm Block cipher Stream cipher Public-key cryptography Cryptographic hash function Message authentication code Random numbers Steganography. Retrieved from " https: Error detection and correction Cryptographic hash functions Hashing Trees data structures.
All articles with unsourced statements Articles with unsourced statements from October Articles with unsourced statements from May Spoken articles Articles with hAudio microformats. Views Read Edit View history. This page was last edited on 7 May , at By using this site, you agree to the Terms of Use and Privacy Policy.