Bitcoin group limited asx exchange rate
25 comments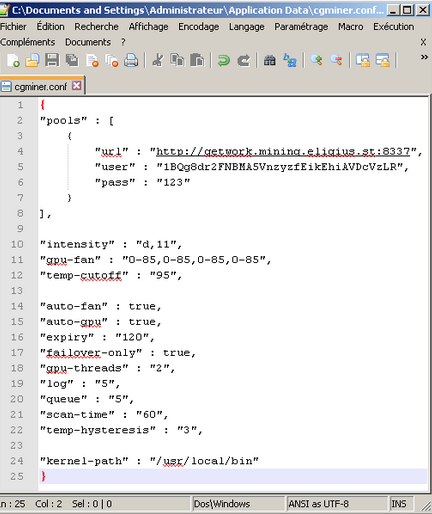
Transfer blockchain unconfirmed transactions
Despite an increase in popularity over recent months amongst botnet operators, malware-powered Bitcoin mining brings little to no financial return, say experts. Security giant McAfee contends in its quarterly threat report PDF that commercial botnet controllers and malware packages have been adding cryptocurrency mining options to their list of services offered. The mining tools - offered alongside botnet task options such as spam runs or distributed denial of service DDoS attacks - put infected machines to use mining Bitcoin.
Unfortunately for the cybercrooks, however, it seems that a botnet-turned-mining rig doesn't actually make much money in real life.
McAfee found that the increasing difficulty of Bitcoin hashes, combined with the attrition rate from malware detections on infected machines, would make turning a profit from botnet mining nearly impossible.
According to researcher estimates, a botnet controller attempting to mine Bitcoin with a 10, system network would initially see a net loss in operations and with increasing difficulty cycles productivity would plateau off without turning much of a profit. That rate becomes even lower when mobile devices are added to the equation. Researchers note that with less powerful processors and limited battery life, mobile devices are ill-equipped to function as dedicated cryptocurrency mining tools, especially when this is done via covert malware infections.
Researchers conclude, therefore, that botnet kingpins are better off avoiding the Bitcoin mining game and sticking with other techniques. That would come as little relief, however, to owners of infected machines who will see their system performance and battery life take a hit whether or not the miner turns a profit. Minds Mastering Machines - Call for papers now open.
The Register - Independent news and views for the tech community. Part of Situation Publishing. Join our daily or weekly newsletters, subscribe to a specific section or set News alerts. The Register uses cookies. But I did log in to the portal, Dave.
Blame everything on 'computer error' — no one will contradict you If you're a Fedora fanboi, this latest release might break your heart a little Microsoft's latest Windows 10 update downs Chrome, Cortana LLVM contributor hits breakpoint, quits citing inclusivity intolerance. Master Amazon Web Services: Get on top of reliability with our best practices webinar El Reg's Serverless Computing London call for papers shuts tonight Now that Kubernetes has won, DigitalOcean takes a late dip in K8s Software dev and deployment luminaries head to Westminster.
If customers' data should be protected, why hand it over to Zuckerberg? My PC is on fire! Can you back it up really, really fast? Geek's Guide Pentagon in uproar: Boffins think they've found the evidence Shocking. Lightning strike knocks out neuro patient's brain implant. Now for some security headaches Silicon can now reconfigure itself with just a jolt of electricity day drone flights? You are like a little baby. How about a full YEAR? Verity Stob Mystery crapper comes a cropper The steaks have never been higher: Swiss Lidl is selling local cannabis Texas residents start naming adopted drains No top-ups, please, I'm a millennial: Lightweight yoof shunning booze like never before.
Thinking of using it to mine Bitcoin? Most read Cambridge Analytica dismantled for good? It just changed its name to Emerdata Democrats need just one more senator and then a miracle to reverse US net neutrality death Take-off crash 'n' burn didn't kill the Concorde, it was just too bloody expensive to maintain Microsoft's latest Windows 10 update downs Chrome, Cortana Exclusive to all press: Atari launches world's best ever games console.
More from The Register. Potentially a hazardous waste dump of child abuse, malware, etc Boffins warn of legal risks from arbitrary data distribution. Malware Engine needs, erm, malware protection Stop appreciating the irony and go install the patch now. Junk food meets junk money: Lloyds Bank bans Bitcoin purchases by credit card customers B-b-b.. Cops seek 4 for aggravated burglary in Midsomer Murders town Fintech workers reportedly targeted.
UK reaches peak Bitcoin as bin firm accepts cryptocurrency 'It's not a publicity stunt,' says BusinessWaste. Massive backlogs, legacy debt, and scarce resources can hinder digital transformation efforts. So, how you can overcome these challenges? Before proceeding we must understand what the definition of the words Certification and Accreditation. Sponsored links Get The Register's Headlines in your inbox daily - quick signup! About us Who we are Under the hood Contact us Advertise with us.
Sign up to our Newsletters Join our daily or weekly newsletters, subscribe to a specific section or set News alerts Subscribe.